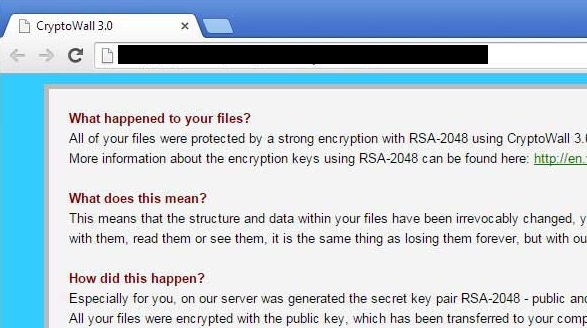
The first variants of the CryptoLocker (and now CryptoWall) virus began to surface in September of 2013. Now, almost 2 years later, we are no closer to stopping this rampant threat. Almost everyone that uses a computer knows someone that has been affected by this destructive virus. From home and business users, to government agencies (and even NASA), this is one of the worst viruses known in history.
The Threat
The reason the Crypto Viruses are so damaging is because of how it behaves. The virus is primarily spread via an email attachment (usually a .zip file with a PDF inside). Usually, it is sent out in a phishing attempt as a fake resume, invoice, tracking number or other important sounding document. The victim usually opens the attachment and begins the infection process. The virus works quickly to extract itself and make a connection to a random server to begin the encryption process. It starts with generating a random 2048-bit RSA key (an encryption key that is nearly impossible to crack) and starts to lock the files on your PC and any networked/external drive that matches the most common file types (like Word, Excel, PDF, QuickBooks and similar files). Once all the file types it is looking for have been locked down, it starts deleting any type of Windows restore points you may be able to use to restore your data. When that job is complete, it pops up a warning message that “You hav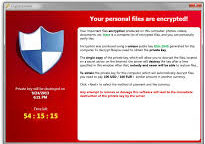 e been infected” and will show a countdown timer with a price associated with getting the “key” to unlock your files. If the timer reaches zero, the price will double and a new timer will begin. If that second timer hits zero, your key will be destroyed and your files will remain locked, unusable and unrecoverable.
e been infected” and will show a countdown timer with a price associated with getting the “key” to unlock your files. If the timer reaches zero, the price will double and a new timer will begin. If that second timer hits zero, your key will be destroyed and your files will remain locked, unusable and unrecoverable.
Your Options
You have a few options. The first is to pay the ransom amount. However, many have reported paying the ransom and they do not receive a key or the key does not work. This is not the best option and it is a true gamble since even if you do pay, you may not get what you paid for. The next option is to try and recover any data from backups. This can include cloud backups, complete system image backups, and devices that were not attached to the system at the time of infection. Depending on how often you backup and the type of method you use, you may be able to recover you data.
Prevention
The best way to protect yourself from the different variants of Crypto is to never put yourself in contact with it. First, never open attachments that are from unknown senders. Also, never download or open any .zip attachment (even if it is from someone you know). Next, always have an anti-virus software active and up to date on any computer you use. Any business should have business grade anti-virus installed on all computers that access the network. Even one unprotected PC can be the gateway into your confidential files. On that same note, all companies should have a business class Intrusion Prevention System (IPS) installed as the first line of defense for your network. An IPS router works as a guard to prevent unwelcome visitors  into your network but allows you, your employees and your approved programs access to the internet. Finally, always have up to date backups. Yes, multiple backups are key in this. Remember the saying “don’t put all your eggs in one basket?” This could not be more applicable to backing up your data. A true backup follows a 3-2-1 method; 3 copies, 2 formats, 1 offsite. This means you have three copies of your data at all times, on two different media locations (like an external hard drive or DVDs) and one copy is constantly backed up to a cloud service.
into your network but allows you, your employees and your approved programs access to the internet. Finally, always have up to date backups. Yes, multiple backups are key in this. Remember the saying “don’t put all your eggs in one basket?” This could not be more applicable to backing up your data. A true backup follows a 3-2-1 method; 3 copies, 2 formats, 1 offsite. This means you have three copies of your data at all times, on two different media locations (like an external hard drive or DVDs) and one copy is constantly backed up to a cloud service.
If you are affected by Crypto or you are looking to protect yourself from becoming a victim, contact your local computer repair center or IT department for assistance.
